Setting up Okta SSO and SCIM
Learn how to set up SSO and SCIM through Okta.
Access RequiredYou must be a workspace Admin (or a relevant custom role) to access the SSO/SCIM page and enable SSO and SCIM in Guru.
Setting up Okta SSO
- Log into your Okta Admin portal. In the left menu, click Applications > Applications.
- Select Browse App Catalog.
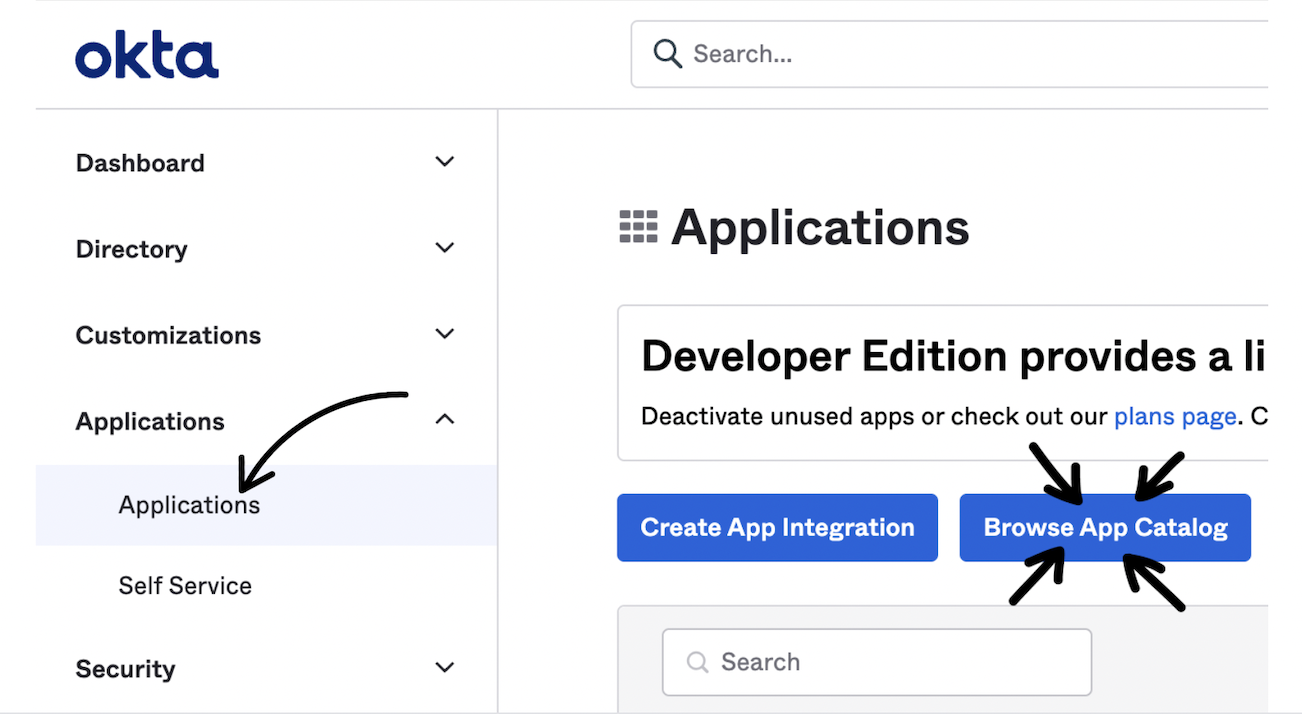
- Search for "Guru", click on the Guru app, then click +Add Integration .
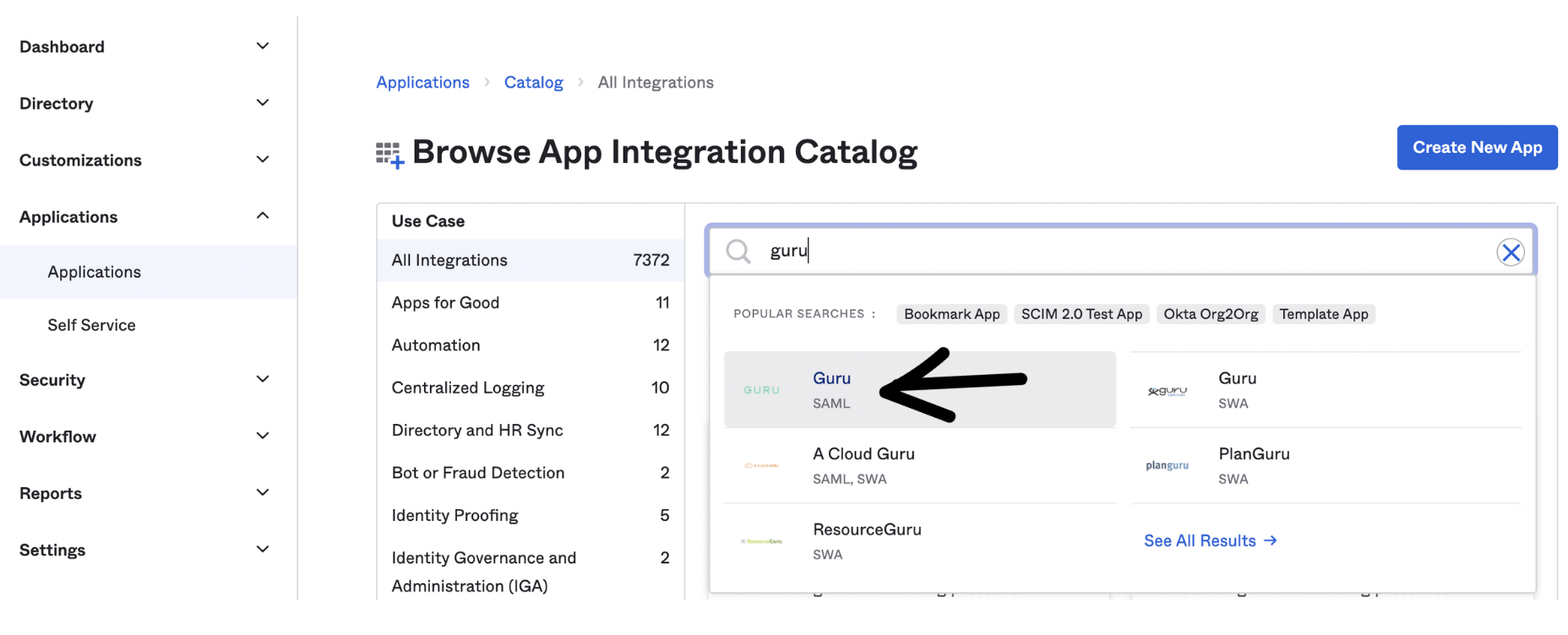
- On the General Settings- Required page, the Application Label should read "Guru". Select your Application Visibility Settings and click Done.
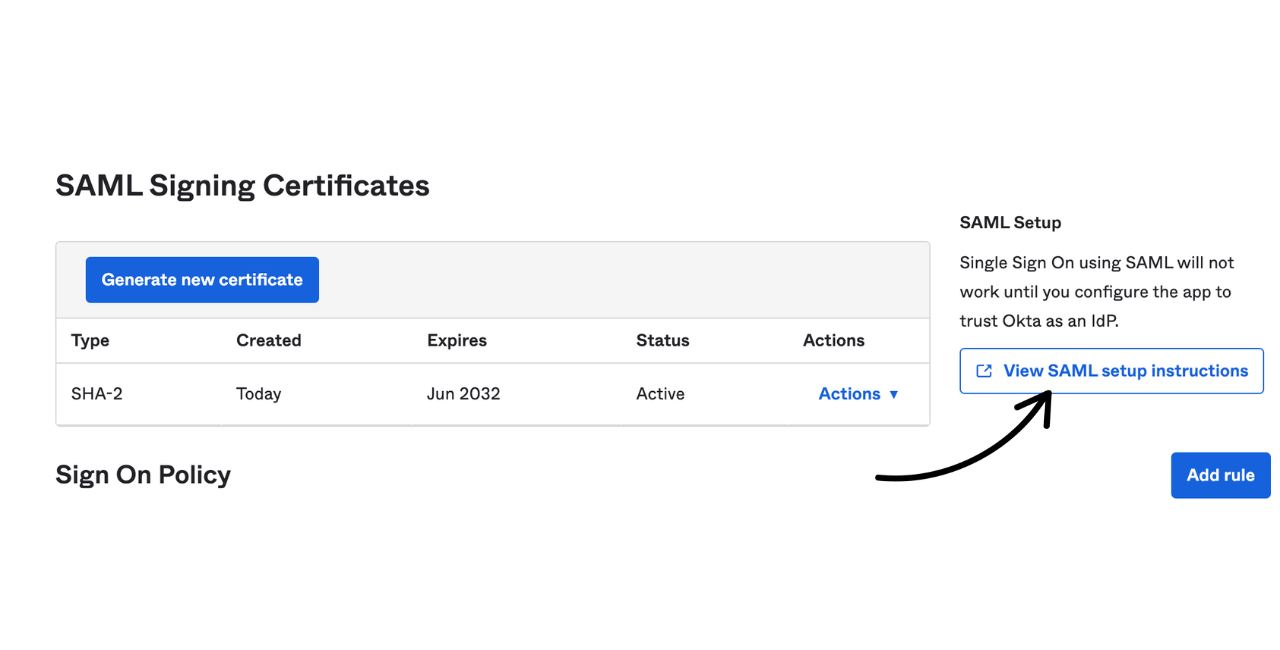
- Click on the Sign On tab and then click the View SAML setup instructions button to open them in a new tab. These instructions will walk you through what values to copy and paste from Okta into Guru on your SSO/SCIM Team Settings page (and vice versa). If you are signed into Okta, these instructions will automatically populate with your team's variables.
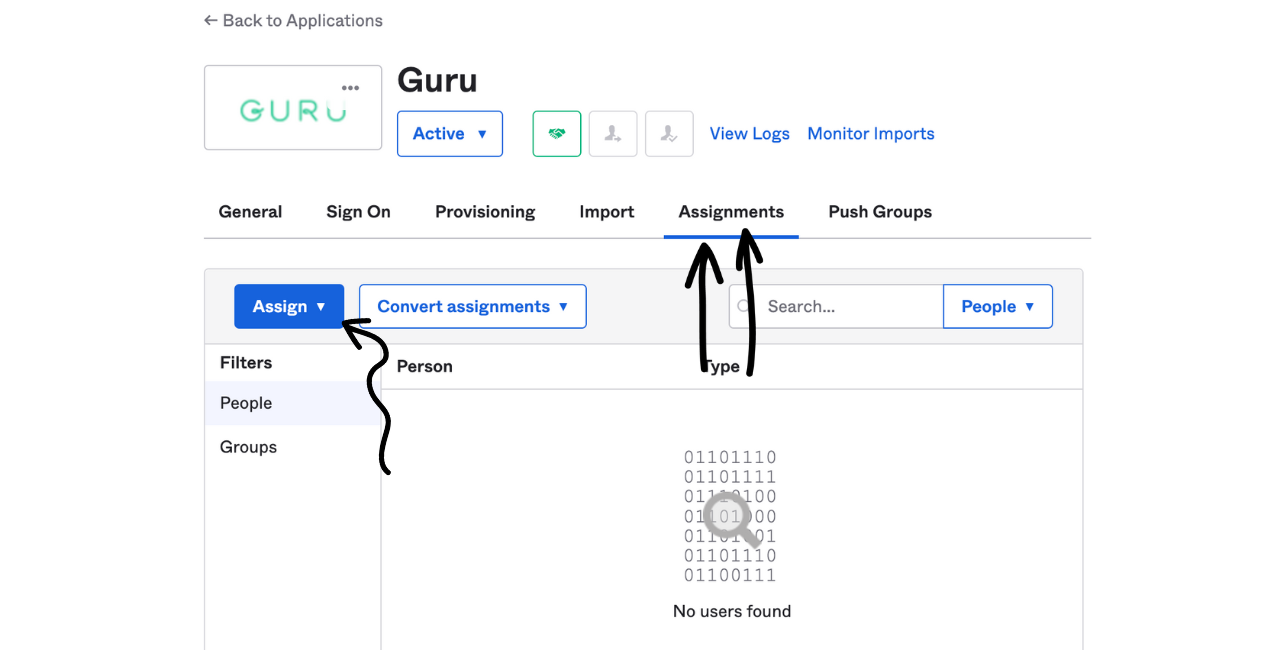
- After completing the steps in Guru, navigate back to Okta. Close the setup instructions and click on the Assignments tabs and assign People and/or Groups to the Guru application in Okta.
- Finally, ask users to return to their Okta Dashboard and click on the Guru icon to log into Guru.
Setting up Okta SCIM
- Open the SSO/SCIM tab in Team Settings and toggle "Authorize SCIM Provisioning" to on.
- Inside of the Guru Okta App, navigate to the Provisioning tab and click on the API Integration setting.
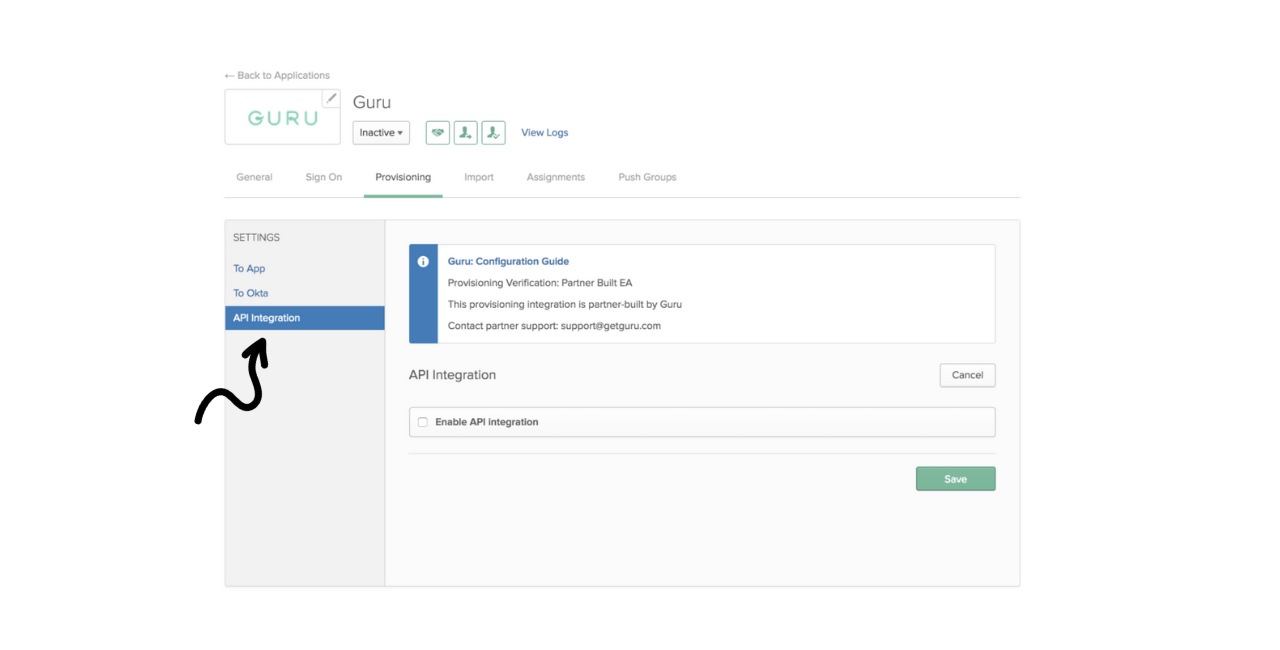
- Click the checkbox to enable the API Integration and then paste in the Username and Token (Password), which can be found under the SCIM Provisioning tab at the bottom of the SSO/SCIM page in Guru, then click Save.
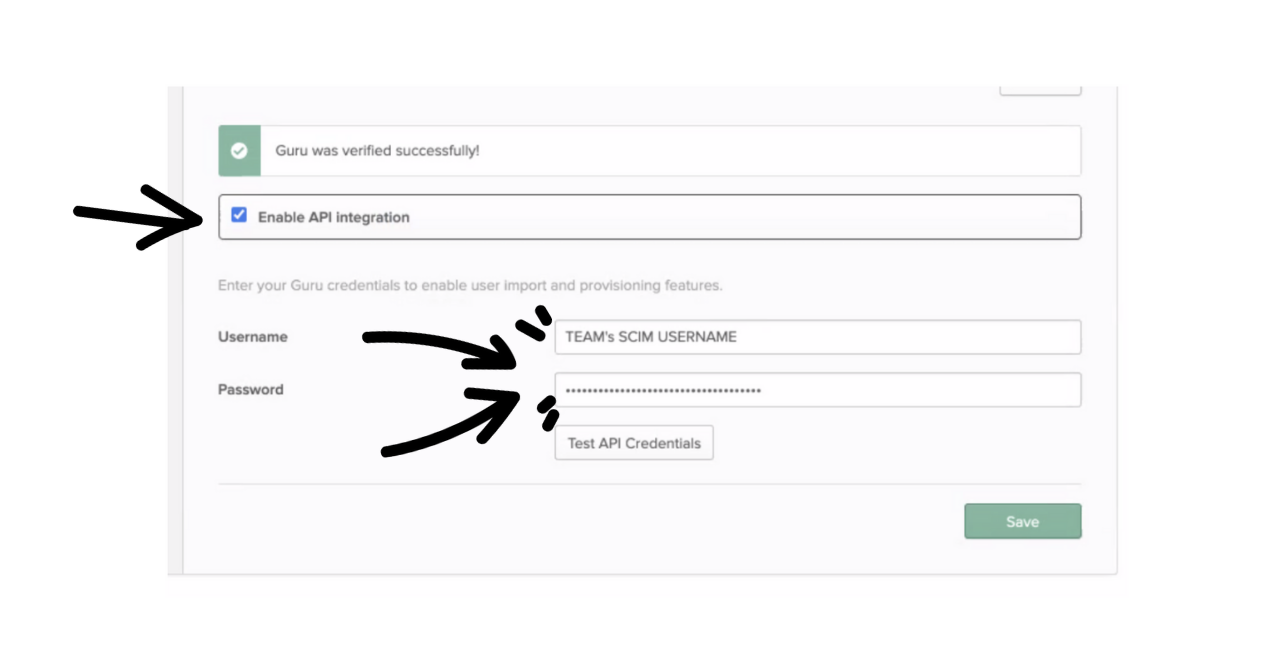
You can click on Test API Credentials to ensure that the credentials are accurate. Click Save.
- Click Edit next to the Provisioning to App settings. From here, you should enable the Create Users, Update User Attributes, and Deactivate Users settings. Under Create Users, ensure that the default username is set to Email. If it is not set to email, you must navigate to the Sign On tab and change it there.
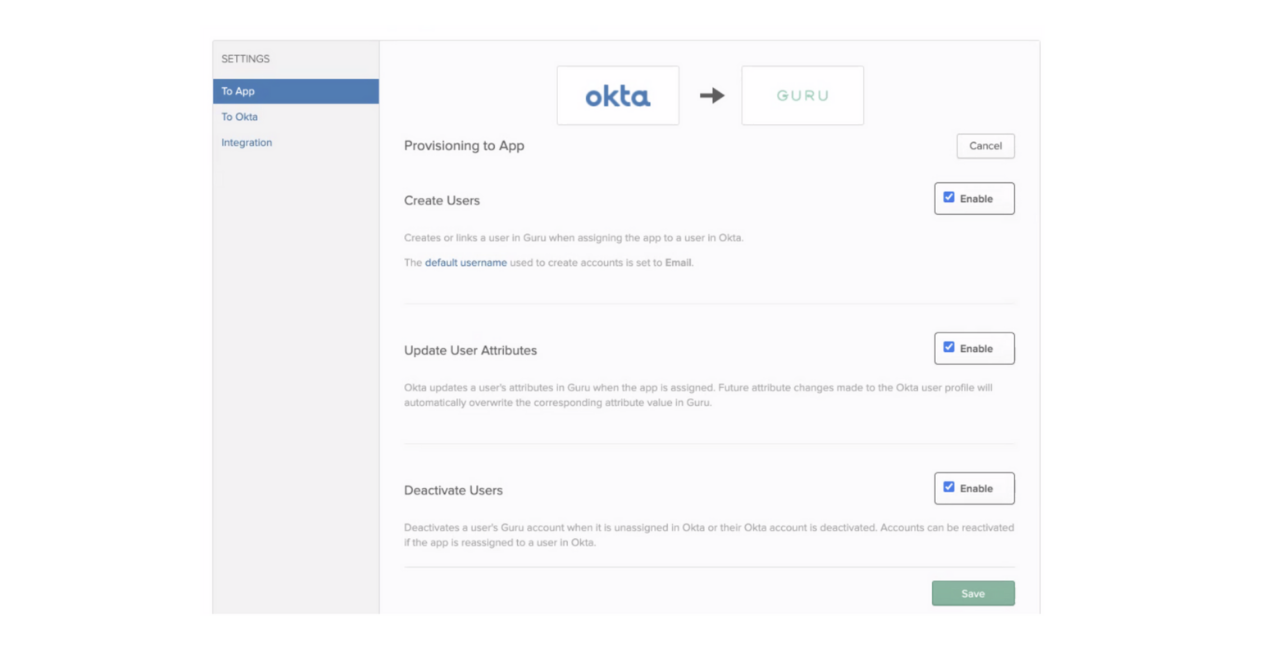
NoteIf Deactivate Users is not enabled, users who are removed from Okta will still exist in Guru and will continue to be billed. Click Save.
- Navigate to the Assignments tab and assign the people or groups you'd like to add to Guru.
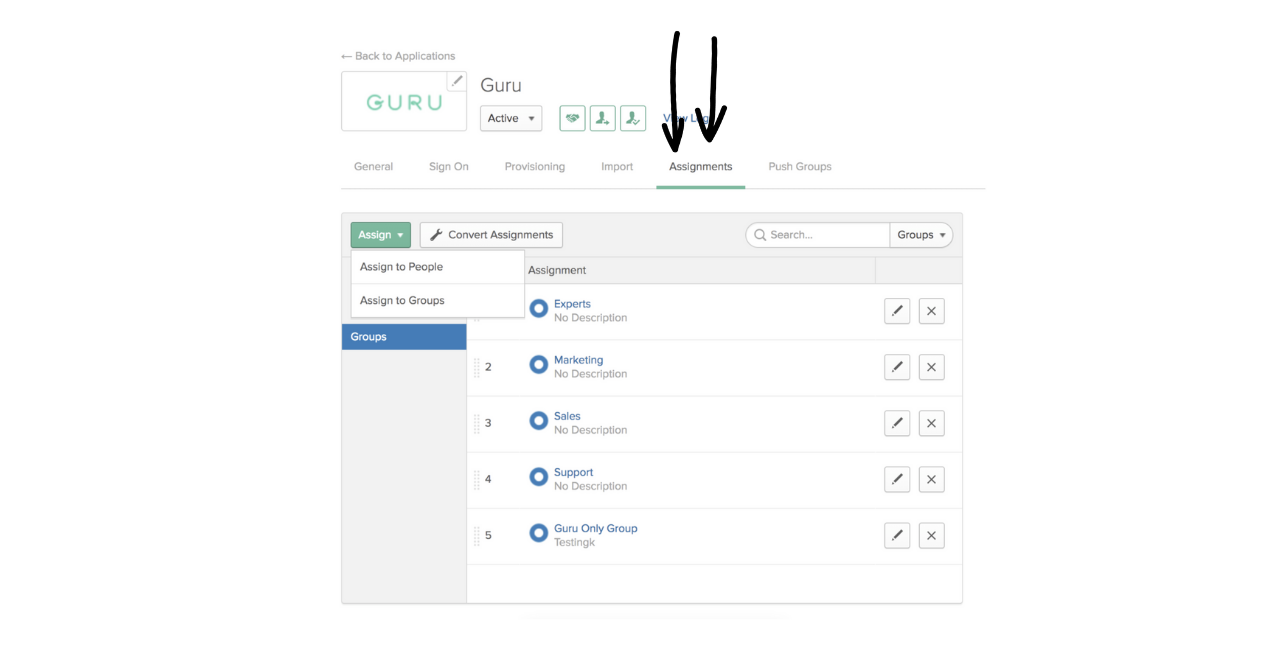
NoteAdding groups in the assignments tab does not create a group in Guru, it simply adds the users in those groups to Guru. This allows you to add users in batches, rather than individually.
- Navigate to the Push Groups tab in Okta. This is where you will add groups from Okta into Guru.
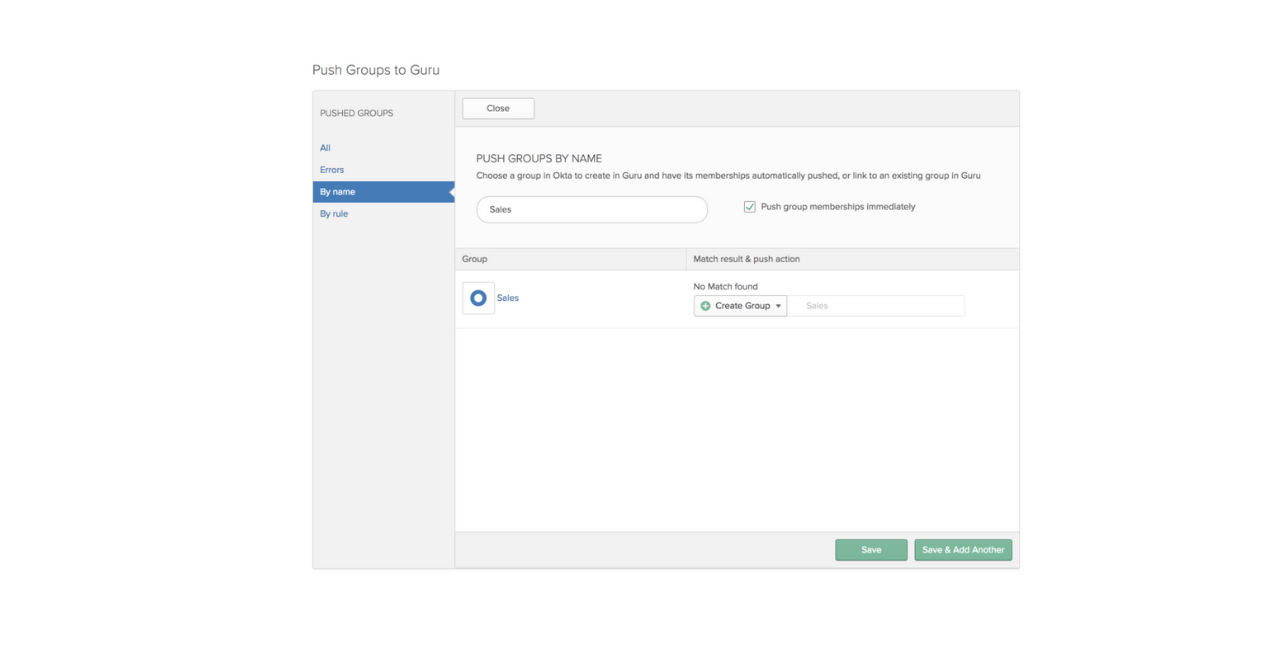
NoteIf the name of the Okta group has the same name as an existing group in Guru, Okta will sync with the Guru group once you click save. This will add the users in the Okta group to the existing Guru group. All users previously in Guru group before sync, will remain in the group.
NoteEnabling Import Groups will bring your Guru Groups (those not provisioned by Okta) into Okta. If Import Groups is disabled, those Groups will not be brought into Okta.
Frequently Asked Questions about authenticating to Guru through Okta
How will users log in to Guru when SSO is turned on?
After Okta SSO has been enabled in Guru, all users must log in to Guru via their Okta Dashboard. Admins will still be able to log into Guru using the web app (with their Guru username and password) as a failsafe, in case of any issues.
Will I have to still invite people to my Guru team?
If you've given your existing team members access to Guru through Okta, they will be able to sign into Guru through Okta. With new team members, it depends on the Provision Type setting in the SSO/SCIM page in Guru. With "Automatically Add Users" enabled, once a user signs in via Okta, a Guru account will be automatically created for them and they will be able to see your team's content.
How do group provisioning and Collection access work?
You can set up users who log into Guru through Okta to join one default Group in Guru. Please note that all new and current users are automatically included in the All Members group. From there, an Admin (or relevant custom role) can add the user to other Groups for them to have the appropriate Collection access.
Updated 3 months ago
